Tighten SSH access to your cloud resources using short-lived SSH certificates

By A Mystery Man Writer
SSH access using public private key based authentication has several drawbacks that could potentially compromise your organization’s SSH access security. SSH certificate based authentication is a great alternative that addresses most of these security problems.

SSH Part 2: Configuring SSH from a Windows 10 Workstation

How to Use SSH Certificates for Scalable, Secure, and More
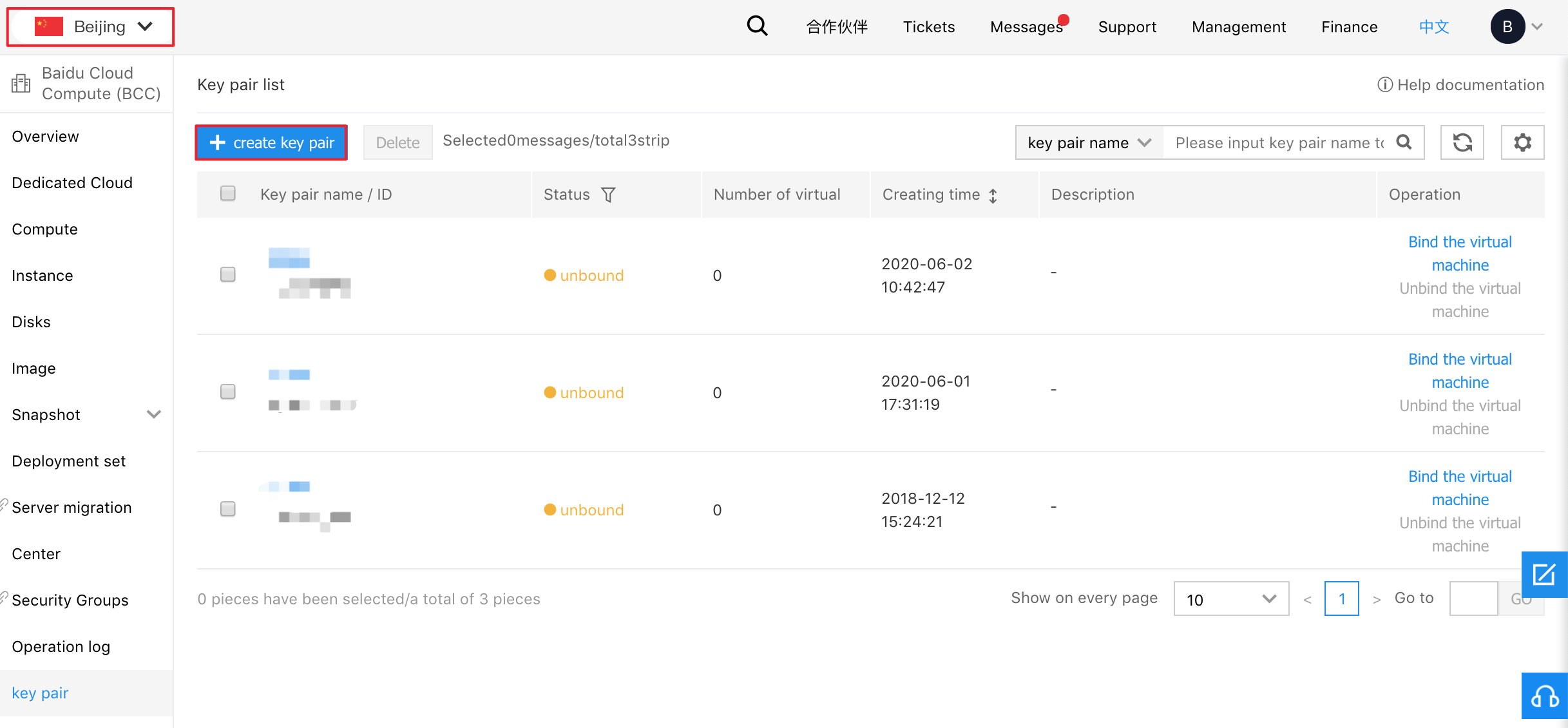
Cloud Compute Service - Key Pair
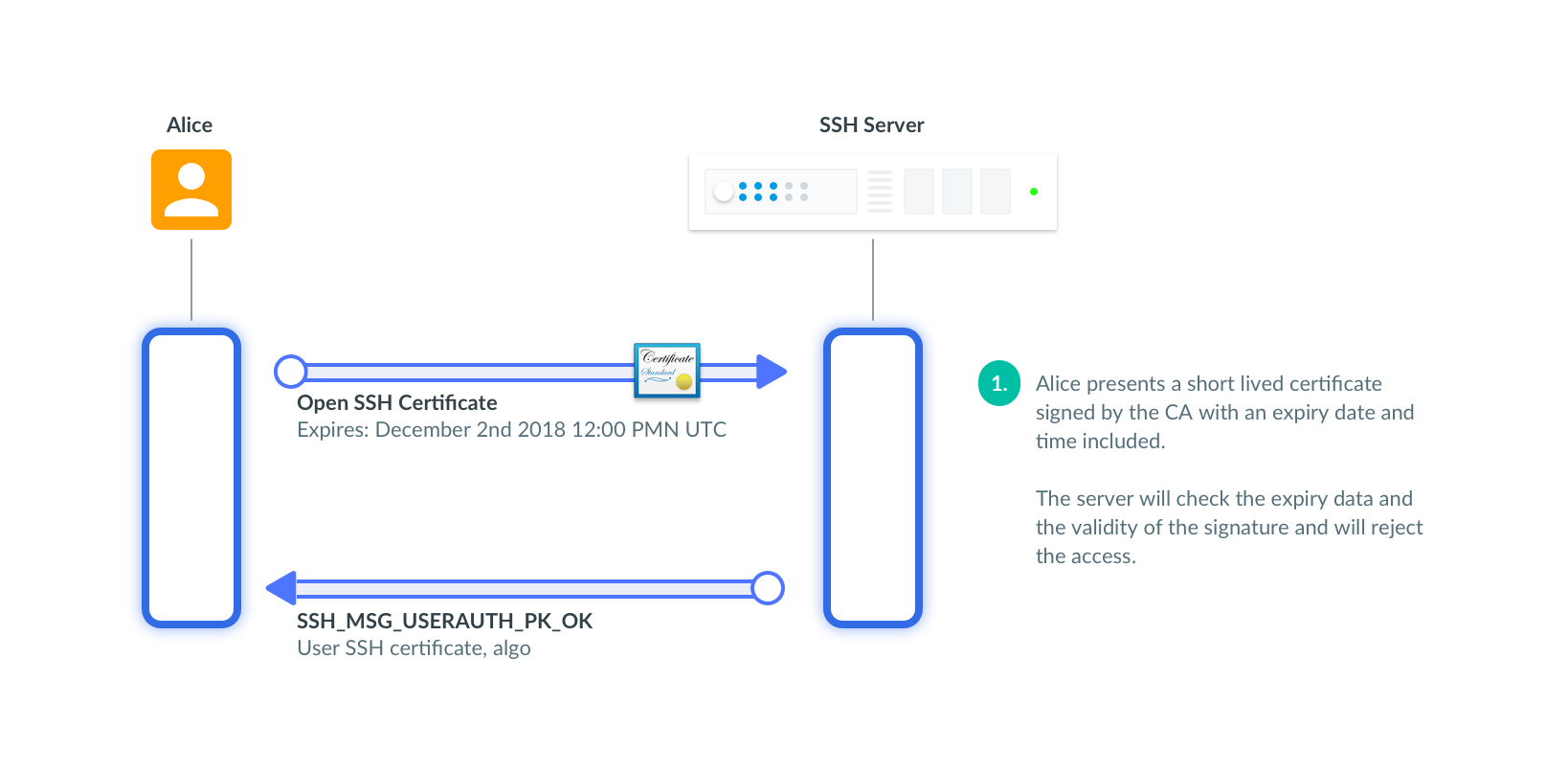
SSH Certificates Security Hardening
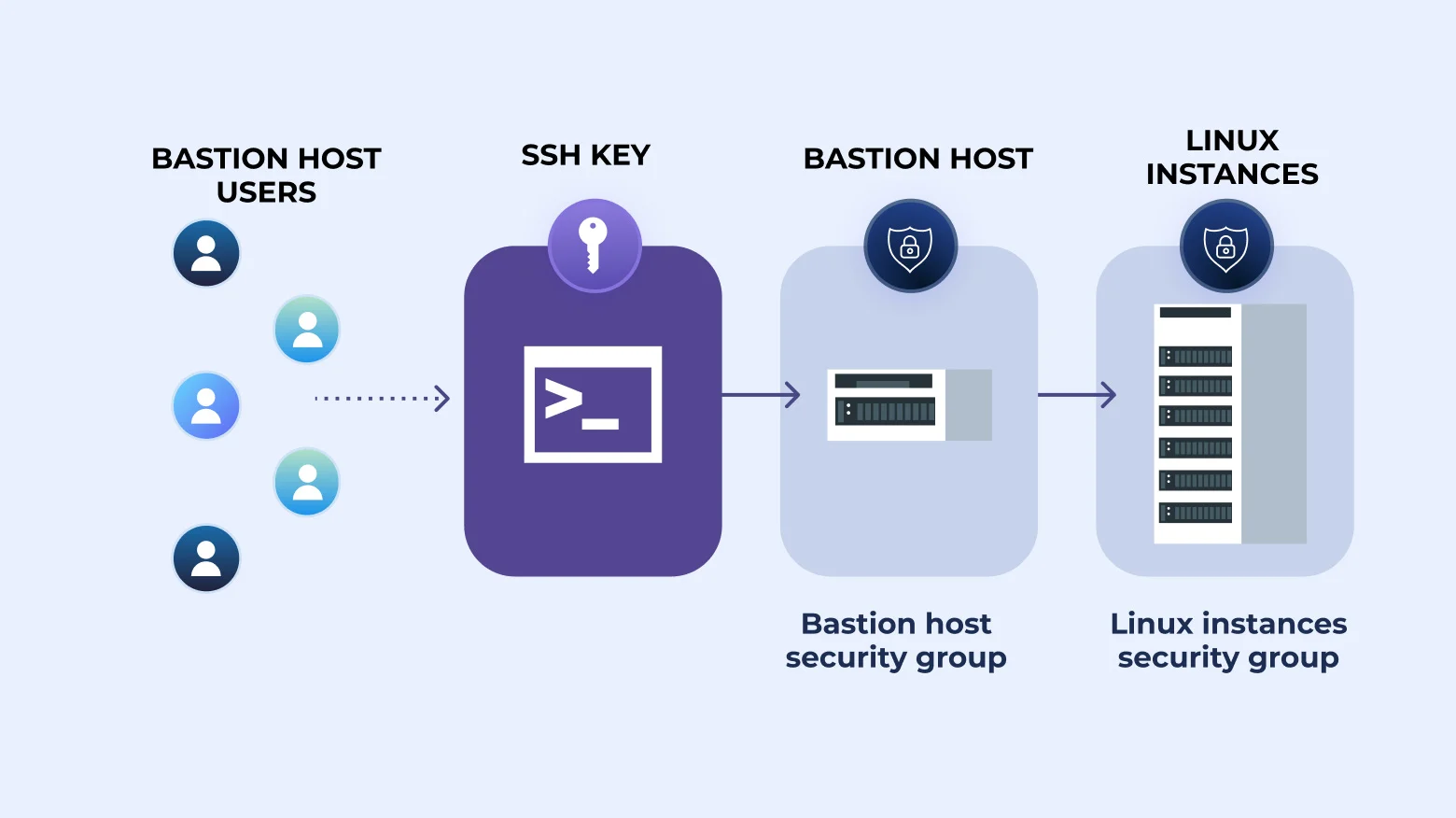
How to SSH Through Bastion With Key [Tutorial]

SSH Part 1: Configuring SSH to Securely Connect to Remote Devices

How to configure and setup SSH certificates for SSH authentication

SSH Key Management Overview & 10 Best Practices

Network Ports in VMware Horizon
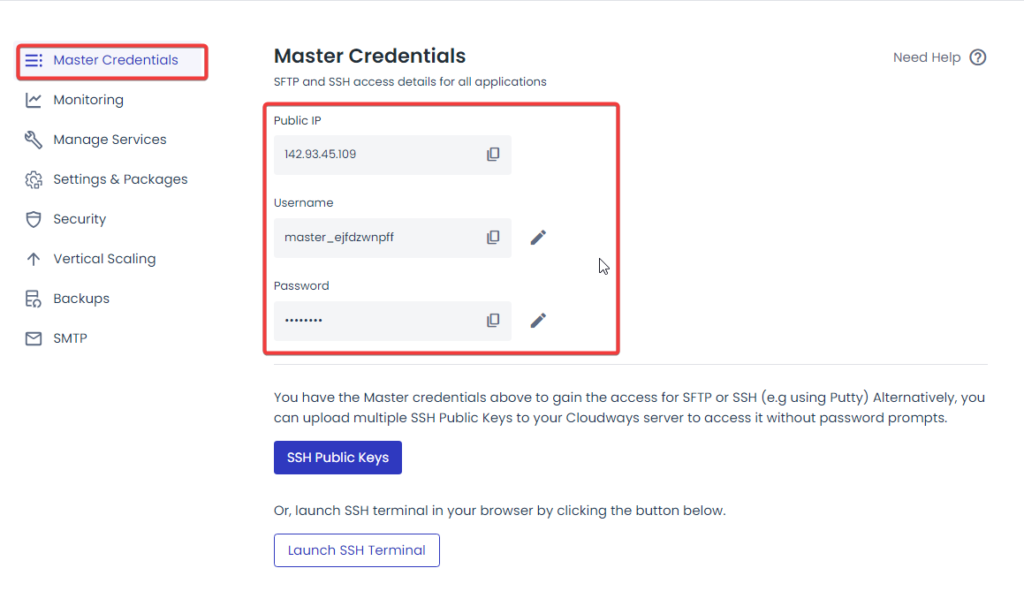
How to Host WordPress on Hosting EC2
Teleport Authentication
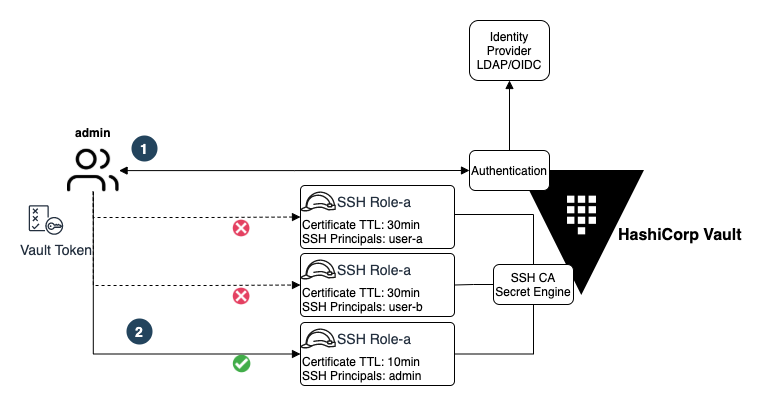
Managing SSH Access at Scale with HashiCorp Vault
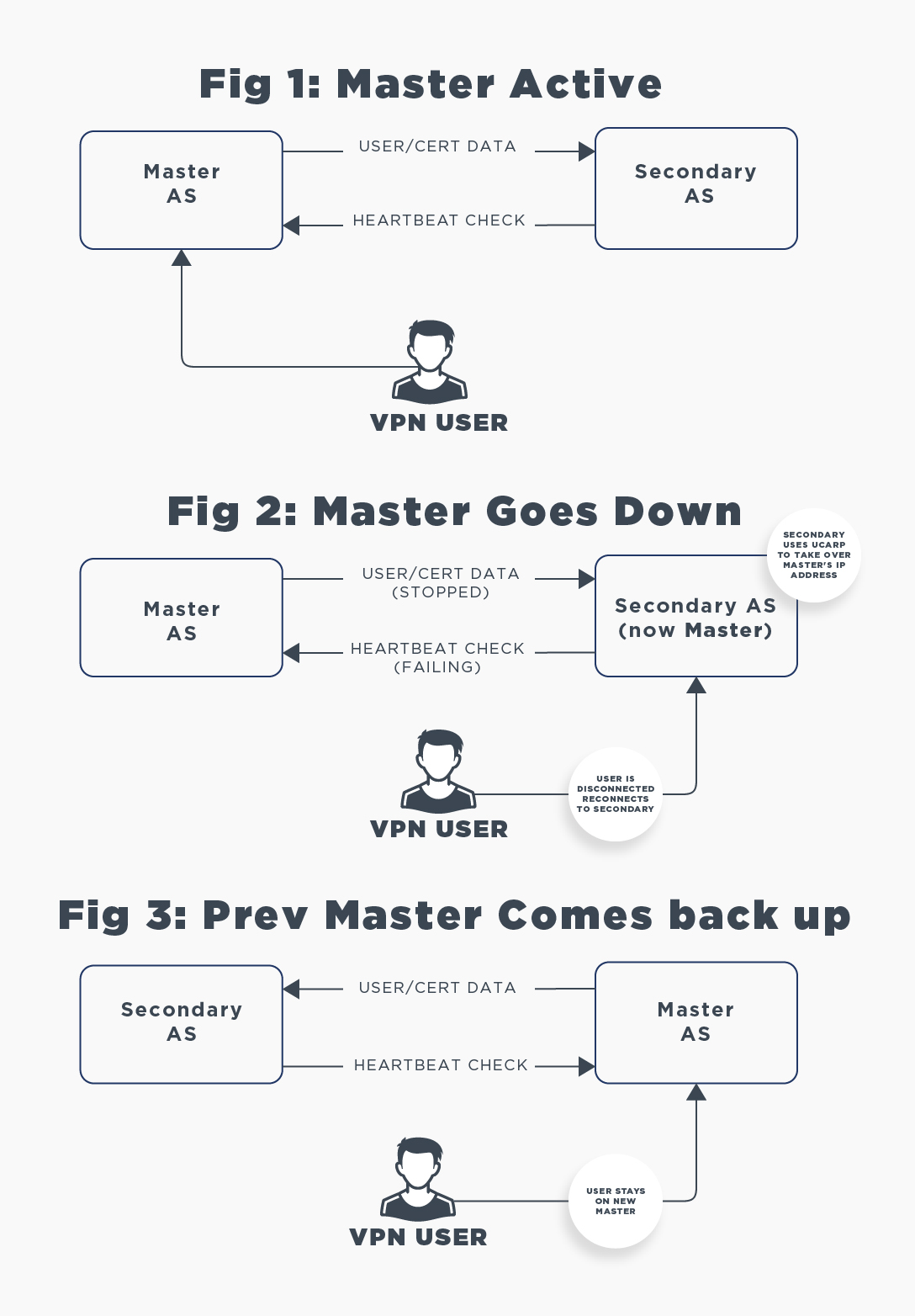
Setting Up High-availability Failover Mode
- Victoria's Secret

- The 15 Best Arm Toning Exercises for Women [Illustrated]: 30 Days

- Womens Padded Sport Bras Sling Tube Top Camisole Medium Support Yoga Sports Bra Fitness Workout Running Camisole Crop Top with Built in Bra

- Buy Assorted Panties & Bloomers for Girls by Marks & Spencer Online

- Ridgewood - Real Hot Yoga